Data Protection | Web Scraping Tool | ScrapeStorm
Abstract:Data protection refers to a series of measures taken to protect important data such as personal and confidential information from risks such as unauthorized access, tampering, leakage and loss. ScrapeStormFree Download
ScrapeStorm is a powerful, no-programming, easy-to-use artificial intelligence web scraping tool.
Introduction
Data protection refers to a series of measures taken to protect important data such as personal and confidential information from risks such as unauthorized access, tampering, leakage and loss. This is not only essential for companies and organizations to fulfill their legal obligations, but also essential for building trust with customers and business partners. With the advancement of digital transformation, due to the popularity of cloud services, IoT devices and remote work, data is distributed everywhere. Traditional perimeter defense security measures alone are far from enough, and multi-level and dynamic protection measures are needed.
Applicable Scene
Data protection is necessary in all fields regardless of the industry, but its importance is particularly prominent in industries that handle large amounts of personal information, such as healthcare, finance, education, and government. For example, hospitals need to securely manage patients’ medical records, and banks need to protect transaction histories and account information from external threats. In addition, companies that provide online services such as e-commerce and SNS need to build and operate systems that comply with laws and regulations such as GDPR (EU General Data Protection Regulation) and Japan’s Personal Information Protection Act because they handle users’ names, contact information, and credit card information. With the expansion of remote work, the opportunities for employees to access business systems from outside the company have also increased, and the introduction of VPN, zero-trust security, and endpoint protection has become one of the important measures.
Pros: By properly implementing data protection, it is possible to prevent damage caused by information leakage and cyber attacks, ultimately avoiding economic losses to the company. In addition, data protection has a significant effect on maintaining and strengthening trust with customers and business partners, thereby enhancing the brand value of the company. In addition, compliance with various laws and regulations can avoid the risk of administrative penalties and fines, helping to ensure credibility when expanding overseas. In recent years, data protection has begun to be evaluated from the perspective of corporate social responsibility (CSR) and ESG investment, and is increasingly regarded as part of business strategy.
Cons: On the other hand, implementing data protection will bring costs and operational burdens. Implementing encryption technology, access control, establishing backup systems, and ensuring the safety of security personnel require a large initial investment and ongoing operational costs. In addition, strengthening security measures will complicate business processes and affect user convenience and work efficiency. In addition, in order to cope with the rapidly evolving means of cyber attacks, it is necessary to keep an eye on the latest threat trends and constantly update countermeasures, which often places a heavy burden on small and medium-sized enterprises.
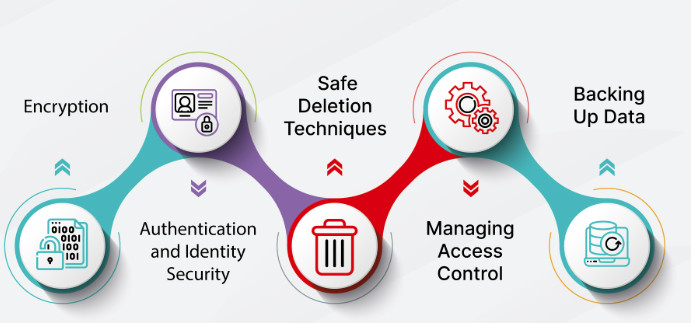
Legend
1. Database protection.

2. Security techniques for database protection.
Related Article
Reference Link
https://commission.europa.eu/law/law-topic/data-protection_en